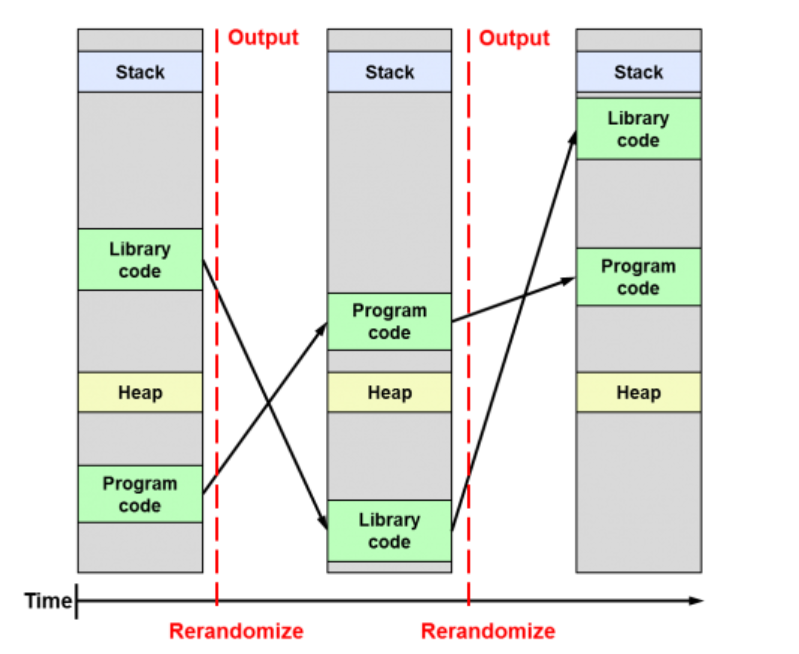
ASLR (Address Space Layout Randomization) is a security technique used to prevent exploitation of memory corruption vulnerabilities, such as buffer overflow attacks. It works by randomly arranging the memory address space of a process each time it runs, making it harder for attackers to predict the location of specific functions, buffers, or data within the memory.
By randomizing the locations of these elements, ASLR makes it more difficult for malicious code to exploit vulnerabilities, as the attacker can’t rely on fixed memory addresses. This adds an extra layer of defense against certain types of cyberattacks.
When and How It Was First Implemented
ASLR (Address Space Layout Randomization) was first introduced in 2001 by Solar Designer, a security researcher, as part of the PaX project (which aimed to provide additional security features for Linux systems). It was later integrated into the Linux kernel and other operating systems over time.
In 2003, ASLR was added to OpenBSD, which was one of the first operating systems to fully implement it. After that, other major operating systems, such as Windows and macOS, started adopting ASLR as a default security measure in the following years.
So, it has been around for quite a while and is now considered a standard security feature in most modern operating systems!


How to Enable ASLR on FreeBSD
Support for Address Space Layout Randomization was added in FreeBSD HEAD (13-CURRENT) in base r343964. It is enabled by default in 14-CURRENT for 64bit architectures, as of base commit b014e0f15bc7. It is enabled by default for 64-bit architectures in FreeBSD 13.2 and later releases.
ASLR is enabled on a per-ABI basis, and is supported on all architectures as of 72091bb39382abba0d71dc23738684bfb4bc2574.
- kern.elf{32,64}.aslr.enable – Enable address map randomization (Default: 1 for 64bit architectures, 0 for 32bit architectures)
- kern.elf{32,64}.aslr.pie_enable – Enable ASLR for Position-Independent Executables (PIE) binaries (Default: 1 for 64bit architectures, 0 for 32bit architectures)
- kern.elf{32,64}.aslr.honor_sbrk – Assume sbrk is used (Default: 0)
- vm.cluster_anon – Cluster anonymous mappings (Default: 1)
Disadvantages of ASLR in FreeBSD:
Performance Overhead:
ASLR introduces additional computation to randomize memory addresses. This can cause a small but noticeable performance overhead, particularly in programs that make frequent use of system calls or deal with memory addresses regularly. While the performance hit may not be significant for most applications, it can become more noticeable in high-performance or latency-sensitive environments.
Tests on the tier 1 64-bit architectures demonstrated that the ASLR is stable and does not result in noticeable performance degradation, therefore it should be safe to enable this mechanism by default. Moreover its effectiveness is increased for PIE (Position Independent Executable) binaries. Thanks to commit 9a227a2fd642 (“Enable PIE by default on 64-bit architectures”), building from src is not necessary to have PIE binaries. It is enough to control usage of ASLR in the OS solely by setting the appropriate sysctls.
As for the drawbacks, a consequence of using the ASLR is more significant VM fragmentation, hence the issues may be encountered in the systems with a limited address space in high memory consumption cases, such as buildworld. As a result, although the tests on 32-bit architectures with ASLR enabled were mostly on par with what was observed on 64-bit ones, the defaults for the former are not changed at this time. Also, for the sake of safety keep the feature disabled for 32-bit executables on 64-bit machines, too.
Compatibility Issues with Legacy Software:
Some older or legacy applications may not be designed to work with ASLR and may exhibit instability or unexpected behavior. This is because ASLR changes memory locations, and older software might assume fixed addresses, leading to crashes or failures. Debuggers and other tools that rely on knowing the memory layout might also struggle to work properly with ASLR-enabled systems.
Increased Complexity in Exploit Development:
While ASLR is a defense against certain types of exploits (like buffer overflows), it can increase the complexity of attacks that rely on knowing the memory addresses of particular functions or variables. This, however, is more of an advantage in terms of security than a disadvantage, but it can also lead to more sophisticated attacks that might bypass ASLR (e.g., using information leaks or other techniques).
Increased Attack Surface (Side-channel Attacks):
In some scenarios, ASLR can make certain types of side-channel attacks (such as those based on timing or memory access patterns) more feasible, especially if other security measures are not in place. Attackers may use techniques like cache timing attacks to defeat ASLR.
Limited Protection for Some Types of Vulnerabilities:
While ASLR protects against certain kinds of buffer overflow and memory corruption attacks, it does not address other vulnerabilities, such as those in the application logic or in protocols (e.g., SQL injection, XSS). As a result, relying solely on ASLR for security is insufficient.
Randomization Limitations:
In FreeBSD, ASLR randomness may not be as robust or fine-grained as in other systems like Linux. The lack of highly unpredictable entropy sources or the potential for weaker randomization could reduce the effectiveness of ASLR as a security measure.
Leave a Reply
You must be logged in to post a comment.