In this article, we will guide you through setting up your own VPN. If you have a public IP, you can set it up on a BeagleBone Black. Alternatively, if you don’t have a public IP, you can deploy the VPN on an AWS t4g.micro instance. For AWS deployments, it’s recommended to use an Elastic IP to prevent IP changes when the instance is stopped. We will cover the AWS instance deployment process separately.
Setup server on Beaglebone black
Please make sure you have listed items ready
- Beaglebone black.
- 5v power supply or Mini-USB cable.
- Micro-SDHC card 16GB or larger.
- Serial cable such as Adafruit #954 or FTDI TTL232R-3V3 (optional but highly recommended).
- BalenaEtcher installed on windows
Install FreeBSD 13.4 Image on BeagleBone Black
- Download FreeBSD-13.4-RELEASE-arm-armv7-GENERICSD.img from freebsd website.
- Use BalenaEtcher to write the image to SD card
- Insert SD card and boot from SD card. Here I am assuming user knows how to boot new image from SD card and get ssh working. Please follow this link to Flash Image on SD card https://vihaaniotgateway.in/index.php/2025/01/19/setting-up-freebsd-on-beaglebone-black-an-easy-installation-guide/
- Connect Beaglebone black to LAN and login through ssh
Setup OpenVPn server on Beaglebone black/AWS t4g.micro instance
- Install OpenVPN on Your Server
- Configure OpenVPN Server Settings
- Set Up PKI and Configure Environment Variables for EasyRSA
- Generate Server Certificates for Secure Connection
- Create Client Certificates for VPN Access
- Configure OpenVPN Server Settings
- Enable IP Forwarding for Network Traffic Routing
Install OpenVPN on Your Server
pkg install -y openvpn;
mkdir -p /usr/local/etc/openvpn;
cp /usr/local/share/examples/openvpn/sample-config-files/server.conf /usr/local/etc/openvpn/openvpn.conf;
mkdir -p /usr/local/etc/openvpn/easy-rsa;
cp -r /usr/local/share/easy-rsa/* /usr/local/etc/openvpn/easy-rsa;
Set Up PKI and Configure Environment Variables for EasyRSA
cd /usr/local/etc/openvpn/easy-rsa
easyrsa init-pki
vi /usr/local/etc/openvpn/easy-rsa/vars
set_var EASYRSA_REQ_COUNTRY "< >"
set_var EASYRSA_REQ_PROVINCE "< >"
set_var EASYRSA_REQ_CITY "< >"
set_var EASYRSA_REQ_ORG "<Your Organization Name>"
set_var EASYRSA_REQ_EMAIL "<Your Email>"
set_var EASYRSA_REQ_OU "<use your public ip or host name>"
set_var EASYRSA_KEY_SIZE 2048
set_var EASYRSA_CA_EXPIRE 3650
set_var EASYRSA_CERT_EXPIRE 3650
Generate Server Certificates for Secure Connection
easyrsa build-ca nopass
easyrsa build-server-full openvpn-server nopass
easyrsa gen-dh
mkdir -p /usr/local/etc/openvpn/keys;
cd /usr/local/etc/openvpn;
cp -p easy-rsa/pki/ca.crt keys/ca.crt;
cp -p easy-rsa/pki/dh.pem keys/dh.pem;
cp -p easy-rsa/pki/issued/openvpn-server.crt keys/openvpn-server.crt;
cp -p easy-rsa/pki/private/openvpn-server.key keys/openvpn-server.key;
cd /usr/local/etc/openvpn/keys;
openvpn --genkey secret ta.key;
sysrc openvpn_enable="YES";
sysrc openvpn_if="tun";
Configure OpenVPN Server Settings
We are using tcp port 80 because it would be easy to migrate to AWS. There is only one (external n/w interface)difference
between aws and beagle bone black. All steps would be same except pf rules and instance deployement,
cat oprnvpn.conf.patch
--- /usr/local/etc/openvpn/openvpn.conf.orig 2024-12-22 14:10:58.899905000 +0000
+++ /usr/local/etc/openvpn/openvpn.conf 2024-12-22 14:40:56.878042000 +0000
@@ -29,11 +29,12 @@
# on the same machine, use a different port
# number for each one. You will need to
# open up this port on your firewall.
-port 1194
+;port 1194
+port 80
# TCP or UDP server?
-;proto tcp
-proto udp
+proto tcp
+;proto udp
# "dev tun" will create a routed IP tunnel,
# "dev tap" will create an ethernet tunnel.
@@ -83,14 +84,18 @@ dev tun
# and use the peer-fingerprint option.
# See openvpn-examples man page for a
# configuration example.
-ca ca.crt
-cert server.crt
-key server.key # This file should be kept secret
+;ca ca.crt
+;cert server.crt
+;key server.key # This file should be kept secret
+ca /usr/local/etc/openvpn/keys/ca.crt
+cert /usr/local/etc/openvpn/keys/openvpn-server.crt
+key /usr/local/etc/openvpn/keys/openvpn-server.key
+dh /usr/local/etc/openvpn/keys/dh.pem
# Diffie hellman parameters.
# Generate your own with:
# openssl dhparam -out dh2048.pem 2048
-dh dh2048.pem
+;dh dh2048.pem
# Allow to connect to really old OpenVPN versions
# without AEAD support (OpenVPN 2.3.x or older)
@@ -112,7 +117,8 @@ topology subnet
# Each client will be able to reach the server
# on 10.8.0.1. Comment this line out if you are
# ethernet bridging. See the man page for more info.
-server 10.8.0.0 255.255.255.0
+;server 10.8.0.0 255.255.255.0
+server 172.16.100.0 255.255.255.0
# Maintain a record of client <-> virtual IP address
# associations in this file. If OpenVPN goes down or
@@ -220,7 +226,7 @@ ifconfig-pool-persist ipp.txt
# To force clients to only see the server, you
# will also need to appropriately firewall the
# server's TUN/TAP interface.
-;client-to-client
+client-to-client
# Uncomment this directive if multiple clients
# might connect with the same certificate/key
@@ -233,7 +239,7 @@ ifconfig-pool-persist ipp.txt
# CERTIFICATE/KEY PAIRS FOR EACH CLIENT,
# EACH HAVING ITS OWN UNIQUE "COMMON NAME",
# UNCOMMENT THIS LINE.
-;duplicate-cn
+duplicate-cn
# The keepalive directive causes ping-like
# messages to be sent back and forth over
@@ -268,7 +274,8 @@ keepalive 10 120
# systems after creating a dedicated user.
;user openvpn
;group openvpn
-
+user nobody
+group nobody
# The persist options will try to avoid
# accessing certain resources on restart
# that may no longer be accessible because
@@ -307,4 +314,4 @@ verb 3
# Notify the client that when the server restarts so it
# can automatically reconnect.
-explicit-exit-notify 1
\ No newline at end of file
+explicit-exit-notify 1
Enable IP Forwarding for Network Traffic Routing
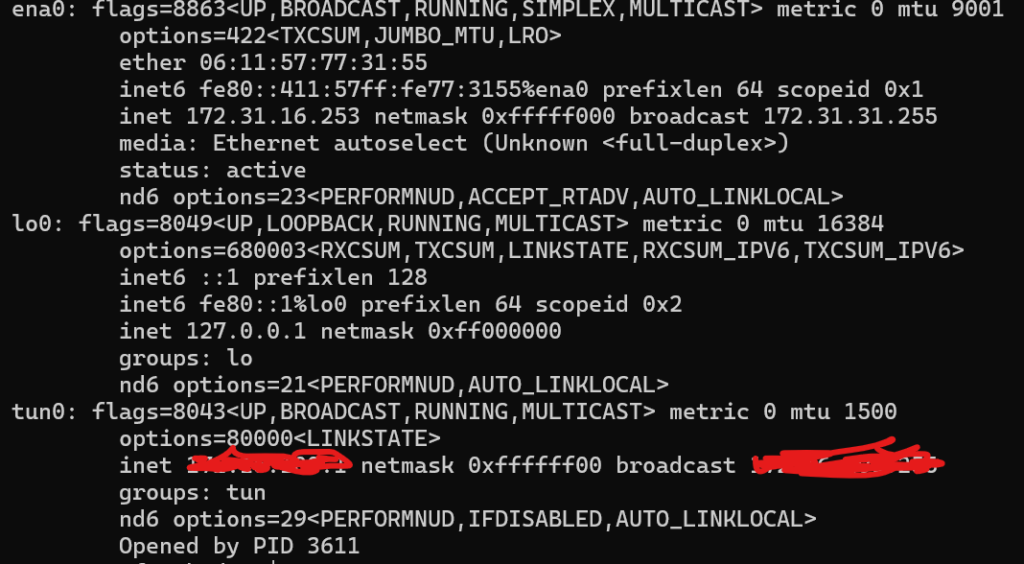
This is needed if you want your internet traffic route through vpn tunnel, otherwise vpn connected devices won’t be able to reach to internet. I am not sure if there is a better way to do this, I was able to make it work by using this approach. Once openvpn is up then you should see tun0 interface up. The screenshot is taken from aws t4g.micro instance. On Beaglebone black also it would look similar except it will display cpsw0 instead of ena0 for externel interface.
service openvpn status
openvpn is running as pid 804.
echo 'pf_load="YES"' >> /boot/loader.conf
echo 'net.inet.ip.forwarding=1' >> /etc/sysctl.conf
**********For AWS Instance Only**************************
echo 'nat on ena0 from 172.16.100.0/24 to any -> (ena0)' > /etc/pf.conf
**************For BeagleBone Black Only*******************
echo 'nat on cpsw0 from 172.16.100.0/24 to any -> (cpsw0)' > /etc/pf.conf
sysrc pf_enable="YES"
sysrc gateway_enable="YES"
reboot
Create Client Certificates for VPN Access
cd /usr/local/etc/openvpn/easy-rsa;
easyrsa build-client-full openvpn-aws-client nopass;
Connect Client On Windows 11
- Install OpenVpn Connect For Windows
- Create .ovpn file and write this data
client
dev tun
proto tcp
remote aws/beaglebone-black-public-ip 80
persist-key
persist-tun
redirect-gateway def1
<ca>
-----BEGIN CERTIFICATE-----
Replace with the ca data cat /usr/local/etc/openvpn/keys/ca.crt
-----END CERTIFICATE-----
</ca>
<cert>
-----BEGIN CERTIFICATE-----
Replace with cert cat /usr/local/etc/openvpn/easy-rsa/pki/issued/openvpn-aws-client.crt
-----END CERTIFICATE-----
</cert>
<key>
Replace with client key cat /usr/local/etc/openvpn/easy-rsa/pki/private/openvpn-aws-client.key
</key>
Import Profile in OpenVpn Connect App
- Install OpenVpn Connect For Windows
- Import above created .ovpn file
- Click on connect, you should be able to connect to vpn
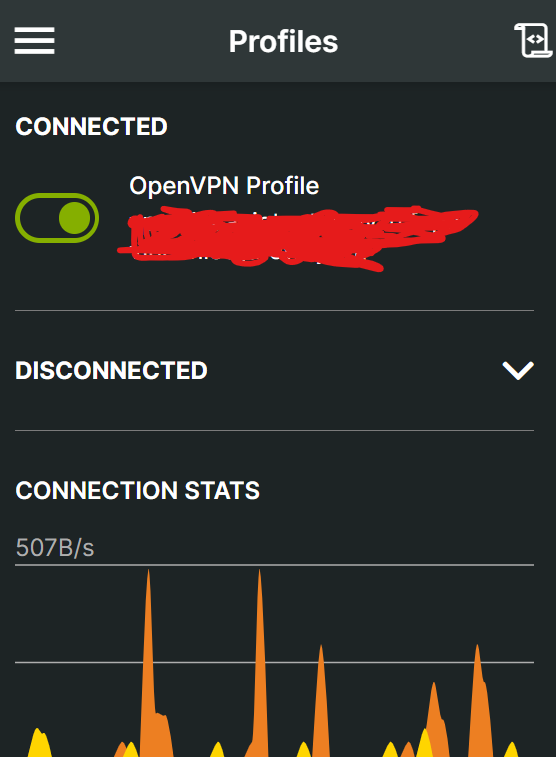
Steps to deploy aws t4g.micro instance To be continued …
Issues faced and References:
Initially I struggled to make internet work on vpn connected devices and found that only pf configuration and ip forwarding made it work. I added this in Beaglebone black configuration openvpn.conf but looks like it is not required as today I configured without this on aws without these changes.
# To assign specific IP addresses to specific
@@ -204,6 +208,7 @@ ifconfig-pool-persist ipp.txt
# or bridge the TUN/TAP interface to the internet
# in order for this to work properly).
;push “redirect-gateway def1 bypass-dhcp”
+push “redirect-gateway def1”
# Certain Windows-specific network settings
# can be pushed to clients, such as DNS
@@ -213,6 +218,8 @@ ifconfig-pool-persist ipp.txt
# DNS servers provided by opendns.com.
;push “dhcp-option DNS 208.67.222.222”
;push “dhcp-option DNS 208.67.220.220”
+push “dhcp-option DNS 8.8.8.8”
+push “dhcp-option DNS 8.8.4.4”

Leave a Reply
You must be logged in to post a comment.